Published on 23 July 2024
Verizon reports that nearly 90% of successful cyberattacks and up to 70% of data breaches originate at the endpoint. Additionally, cybercriminals are accelerating their attack timelines, with most ransomware attacks being executed within 24 hours of initial access, as highlighted in a recent SecureWorks report.
Consequently, organisations are increasingly implementing cybersecurity solutions with real-time threat detection and response capabilities. Three technologies have become particularly popular: endpoint detection and response (EDR), extended detection and response (XDR), and managed detection and response (MDR). Understanding the differences between these solutions is crucial for selecting the right security strategy.
Let’s dive into each one and see how they compare.
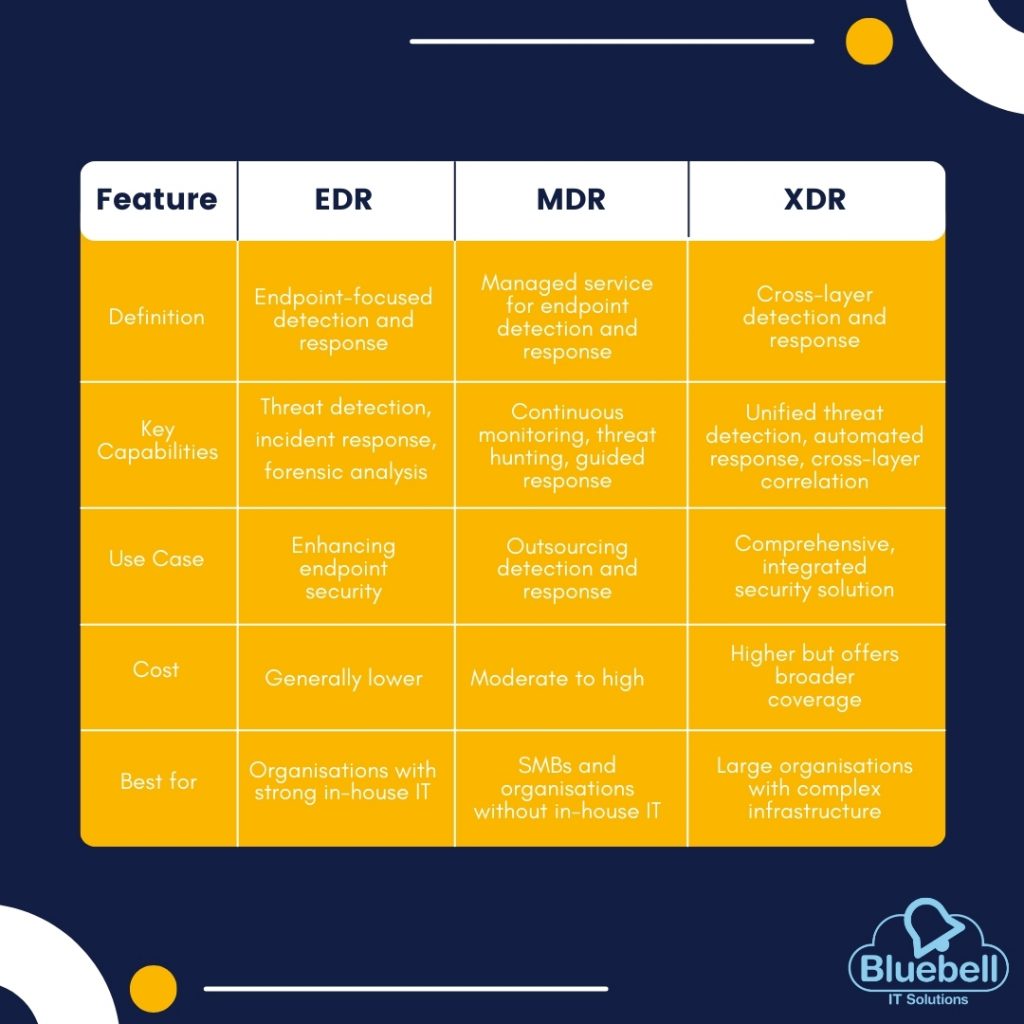
Definition: EDR focuses on monitoring, detecting, and responding to cyber threats at the endpoint level. Endpoints include devices such as computers, mobile phones, and servers
Key Features:
• Threat Detection: EDR systems continuously monitor endpoint activities to detect suspicious behaviour or known attack patterns.
• Incident Response: They provide tools for responding to and mitigating threats, such as isolating infected devices or removing malicious files.
• Forensic Analysis: EDR solutions offer detailed data collection and analysis to understand the nature and source of threats.
Traditional endpoint security and antivirus solutions are reactive, meaning they can only detect threats with known patterns and signatures, but they fall short when it comes to identifying novel threats or zero-day malware. Modern malware, however, appears in several forms, using techniques like encryption, obfuscation, and self-modification to alter their signatures and evade traditional security measures.
Traditional endpoint security and antivirus software rely on known patterns and signatures to reactively detect threats, often missing new or zero-day malware that can evade detection through encryption, obfuscation, or self-modification.
Endpoint Detection and Response (EDR) takes a proactive, behaviour-based approach. It continuously monitors and analyses endpoint events and behaviours in real-time using AI and ML to detect and block zero-day and polymorphic malware. EDR also offers advanced threat response capabilities, including identifying compromised processes, isolating infected endpoints, alerting security teams, and providing detailed forensic data for investigations.
Use Case: EDR is particularly effective for organisations looking to strengthen their endpoint security by gaining visibility into device-level threats and responding swiftly to incidents.
Definition: XDR is an integrated security approach that goes beyond EDR by correlating data across multiple security layers, including endpoints, networks, servers, and cloud workloads.
Key Features:
• Unified Threat Detection: XDR collects and analyses data from various security tools to provide a comprehensive view of threats.
• Automated Response: It automates the response to detected threats, reducing the time to mitigate incidents.
• Cross-Layer Correlation: XDR correlates data across different security domains to identify sophisticated attacks that might evade single-layer defences.
• Enhanced Visibility: Provides greater visibility into the entire security environment, enabling more effective threat detection and response.
Use Case: XDR is ideal for organisations seeking a holistic security solution that integrates multiple security tools and provides a unified view of their security posture.
EDR focuses on monitoring and detecting threats specifically at endpoints. In contrast, XDR expands beyond endpoints to monitor and analyse security signals across networks, clouds, and email security systems. This broader approach offers comprehensive threat coverage across the entire IT environment, making it ideal for organisations with complex infrastructures or high vulnerability to cyberattacks. XDR scales effectively by integrating multiple data sources, ensuring thorough security coverage regardless of organisational size.
Definition: MDR is a service that combines advanced technology with human expertise to provide comprehensive threat detection, analysis, and response.
Key Features:
• 24/7 Monitoring: MDR services offer round-the-clock monitoring of an organisation’s network and systems.
• Expert Analysis: Security experts analyse detected threats and provide actionable insights and guidance.
• Proactive Threat Hunting: MDR involves actively searching for threats rather than waiting for alerts.
• Incident Response Support: It includes assistance in responding to and mitigating incidents.
Use Case: MDR is suitable for organisations that lack the in-house resources or expertise to manage advanced threat detection and response on their own. It offers a balance of technology and human intelligence.
MDR is a managed threat detection and response service offered by external security providers, not a specific technology. Running a dedicated Security Operations Centre (SOC) can be expensive and demanding, prompting many organisations to outsource threat hunting, monitoring, detection, and response to MDR providers with the necessary resources and skills. MDR services are particularly beneficial for small and medium-sized businesses (SMBs) looking for robust threat monitoring and response capabilities without the overhead of internal management and infrastructure.
Choosing the right detection and response solution is vital for robust cybersecurity. Whether you are strengthening endpoint security with EDR, seeking comprehensive managed services with MDR, or looking for an integrated, cross-layered approach with XDR, understanding these solutions’ unique benefits is crucial.
Need help deciding which solution is best for your organisation? Contact Bluebell IT Solutions for expert advice and a tailored cybersecurity strategy to protect against evolving threats.

© 2025 Bluebell IT Solutions - All rights reserved
SEO and Website Design by Loop Digital